Lateral Movement
Lateral movement is the group of techniques used by attackers to move around a network. Once an attacker has gained access to the first machine of a network, moving is essential for many reasons, including the following: - Reaching our goals as attackers - Bypassing network restrictions in place - Establishing additional points of entry to the network - Creating confusion and avoid detection.
+------------------+
| Psexec |
+------------------+
+------------------+
| WinRM |
+------------------+
+------------------+ +------------------+ +------------------+
| MACHINE 1 | | SSH | | MACHINE 2 |
+------------------+ +------------------+ +------------------+
+------------------+
| RDP |
+------------------+
+------------------+
| VNC |
+------------------+
-
Remote Desktop Protocol(RDP) - is a remote access/management protocol that gives us GUI access to a target host -
PowerShell Remoting - also referred to as PSRemoting or Windows Remote Management (WinRM) access, is a remote access protocol that allows us to run commands or enter an interactive command-line session on a remote host using PowerShell
Remote Desktop
Using PowerView, we could use the Get-NetLocalGroupMember function to begin enumerating members of the Remote Desktop Users group on a given host.
Enumerating the Remote Desktop Users Group
Get-NetLocalGroupMember -ComputerName ACADEMY-EA-MS01 -GroupName "Remote Desktop Users"
|->
ComputerName : ACADEMY-EA-MS01
GroupName : Remote Desktop Users
MemberName : INLANEFREIGHT\Domain Users
SID : S-1-5-21-3842939050-3880317879-2865463114-513
IsGroup : True
IsDomain : UNKNOWN
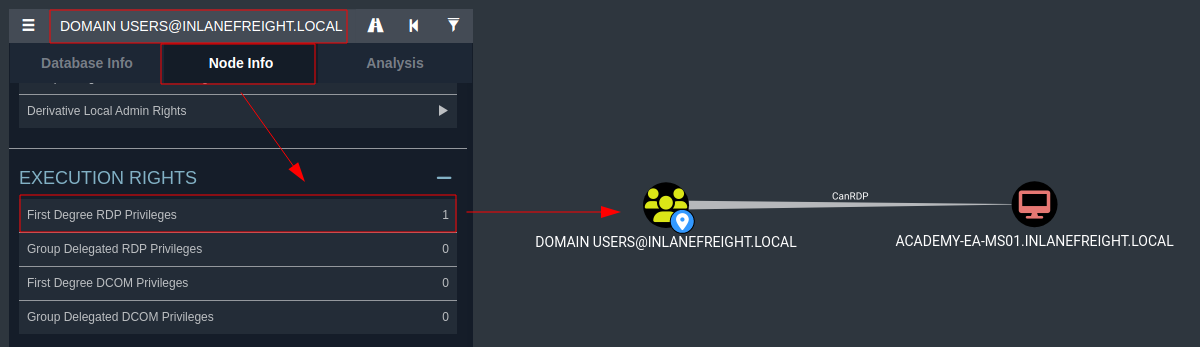
- From the information above, we can see that all Domain Users (meaning
allusers in the domain) can RDP to this host.
Checking the Domain Users Group's Local Admin & Execution Rights using BloodHound
WinRM
Enumerating the Remote Management Users Group
Get-NetLocalGroupMember -ComputerName ACADEMY-EA-MS01 -GroupName "Remote Management Users"
|->
ComputerName : ACADEMY-EA-MS01
GroupName : Remote Management Users
MemberName : INLANEFREIGHT\forend
SID : S-1-5-21-3842939050-3880317879-2865463114-5614
IsGroup : False
IsDomain : UNKNOWN
Using the Cypher Query in BloodHound
Find WinRM Users
MATCH p1=shortestPath((u1:User)-[r1:MemberOf*1..]->(g1:Group)) MATCH p2=(u1)-[:CanPSRemote*1..]->(c:Computer) RETURN p2

Spawning Processes Remotely
Psexec
- Ports: 445/TCP (SMB)
- Required Group Memberships: Administrators
winrm - Remote Process Creation
- Ports: 5985/TCP (WinRM HTTP) or 5986/TCP (WinRM HTTPS)
- Required Group Memberships: Remote Management Users
cs - Remote Services Creation
- Ports:
- 135/TCP, 49152-65535/TCP (DCE/RPC)
- 445/TCP (RPC over SMB Named Pipes)
- 139/TCP (RPC over SMB Named Pipes)
- Required Group Memberships: Administrators