SSH local port forwarding
Port Forwarding in Context
Port forwarding is a technique that allows us to redirect a communication request from one port to another. Port forwarding uses TCP as the primary communication layer to provide interactive communication for the forwarded port. However, different application layer protocols such as SSH or even SOCKS (non-application layer) can be used to encapsulate the forwarded traffic. This can be effective in bypassing firewalls and using existing services on your compromised host to pivot to other networks.
📝 Forward one ports
Scanning before port forwarding (attack host)
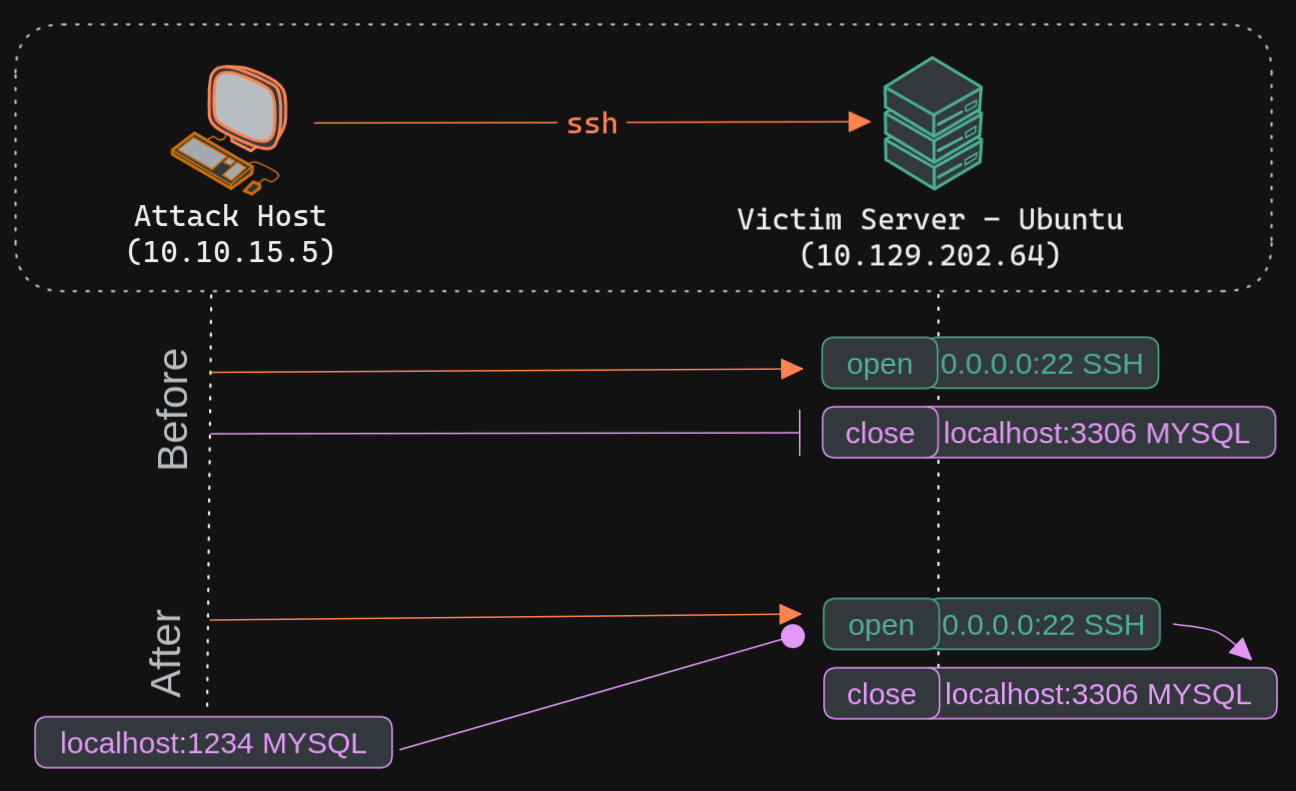
The Nmap output shows that the SSH port is open. But MySQL port is close. To access the MySQL service, we can either SSH into the server and access MySQL from inside the Target server, or we can port forward it to our localhost on port 1234 and access it locally.
Executing the Local Port Forward (attack host)
The -L command tells the SSH client to request the SSH server to forward all the data we send via the port 1234 to localhost:3306 on the Target server. By doing this, we should be able to access the MySQL service locally on port 1234. We can use Netstat or Nmap to query our local host on 1234 port to verify whether the MySQL service was forwarded.
Confirming Port Forward with Netstat (attack host)
netstat -antp | grep 1234
|->
tcp 0 0 127.0.0.1:1234 0.0.0.0:* LISTEN 4034/ssh
tcp6 0 0 ::1:1234 :::* LISTEN 4034/ssh
sudo nmap -v -sV -p 1234 localhost
|->
PORT STATE SERVICE VERSION
1234/tcp open mysql MySQL 8.0.28-0ubuntu0.20.04.3